Protect Innovations
with Expert Insights
ENKI WhiteHat provides unparalleled security
with unrivaled expertise.
Protect Innovation with Expert Insight
Providing unparalleled security
with unrivaled expertise
Protect Innovation
with Expert Insight
ENKI WhiteHat provides unparalleled security
with unrivaled expertise.
ENKI WhiteHat Service
A cybersecurity company specializing in offensive security, preemptively responding to cyber threats from a hacker's perspective
A cybersecurity company specializing in offensive security, preemptively responding to cyber threats from a hacker's perspective
Offensive Security Consulting
The only way for a company to know if they are vulnerable to cyber threats is to see it from the attacker's perspective. Companies are looking for cyber threats that they are facing, from system paralysis to customer information leakage.
Offensive Security Consulting
The only way for a company to know if they are vulnerable to cyber threats is to see it from the attacker's perspective. Companies are looking for cyber threats that they are facing, from system paralysis to customer information leakage.
Offensive Security Consulting
The only way for a company to know if they are vulnerable to cyber threats is to see it from the attacker's perspective. Companies are looking for cyber threats that they are facing, from system paralysis to customer information leakage.
Cyber Threat Intelligence
Provides threat information by analyzing the strategies and tactics of the four major cyber threat countries and major cyber criminal groups such as North Korea, China, Russia, and Iran.{{}}
Cyber Threat Intelligence
Provides threat information by analyzing the strategies and tactics of the four major cyber threat countries and major cyber criminal groups such as North Korea, China, Russia, and Iran.{{}}
Cyber Threat Intelligence
Provides threat information by analyzing the strategies and tactics of the four major cyber threat countries and major cyber criminal groups such as North Korea, China, Russia, and Iran.{{}}
Cyber security education, training
White hackers provide hands-on educational services, ranging from browser and system hacking to reverse engineering.
Cyber security education, training
White hackers provide hands-on educational services, ranging from browser and system hacking to reverse engineering.
Cyber security education, training
White hackers provide hands-on educational services, ranging from browser and system hacking to reverse engineering.
Trusted by the leaders
Major domestic and international companies and institutions are partnering with EnkiWhiteHat.
ENKI WhiteHat is trusted by major enterprises and institutions both in and outside Korea.






ENKI WhiteHat Product
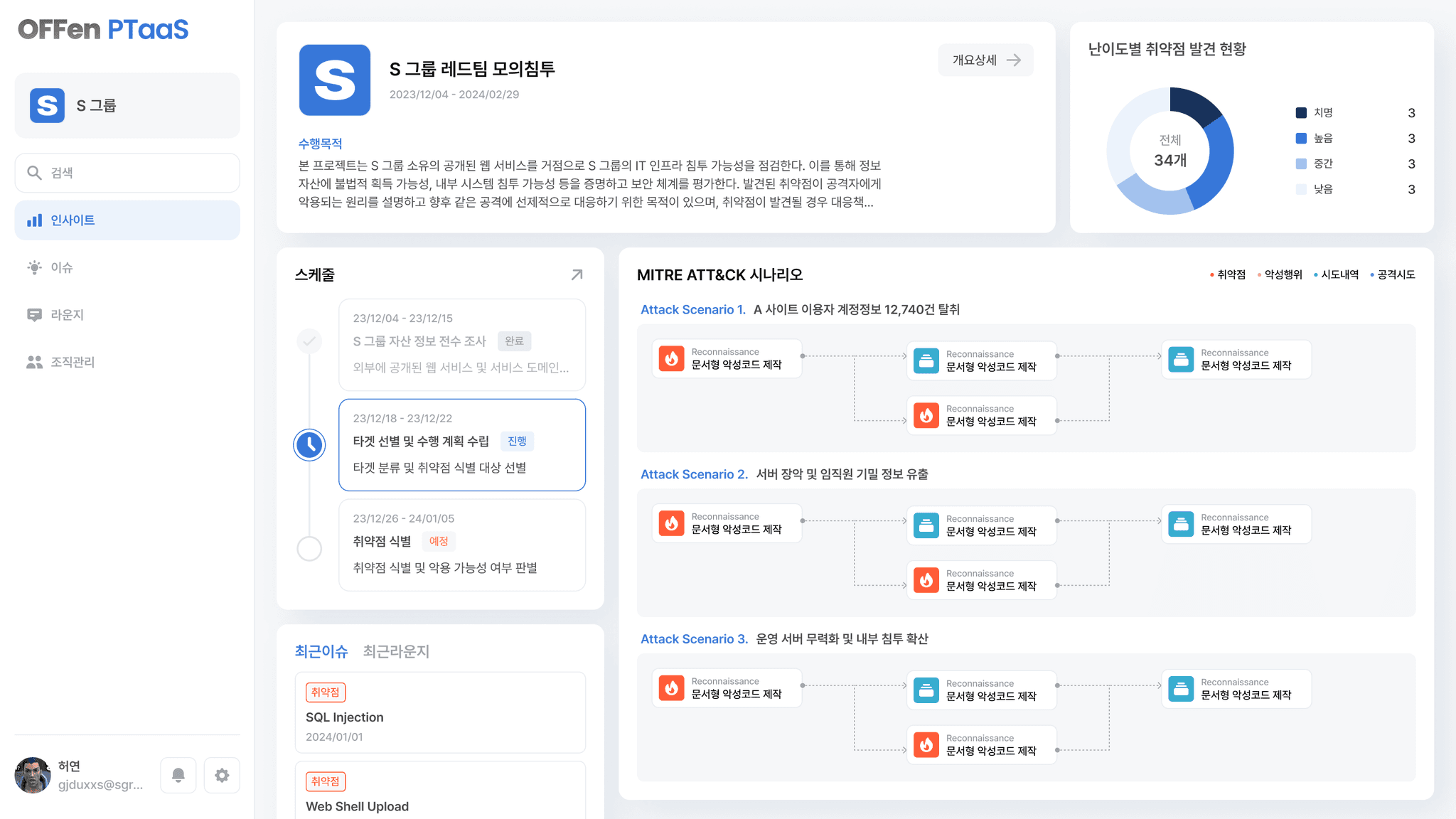
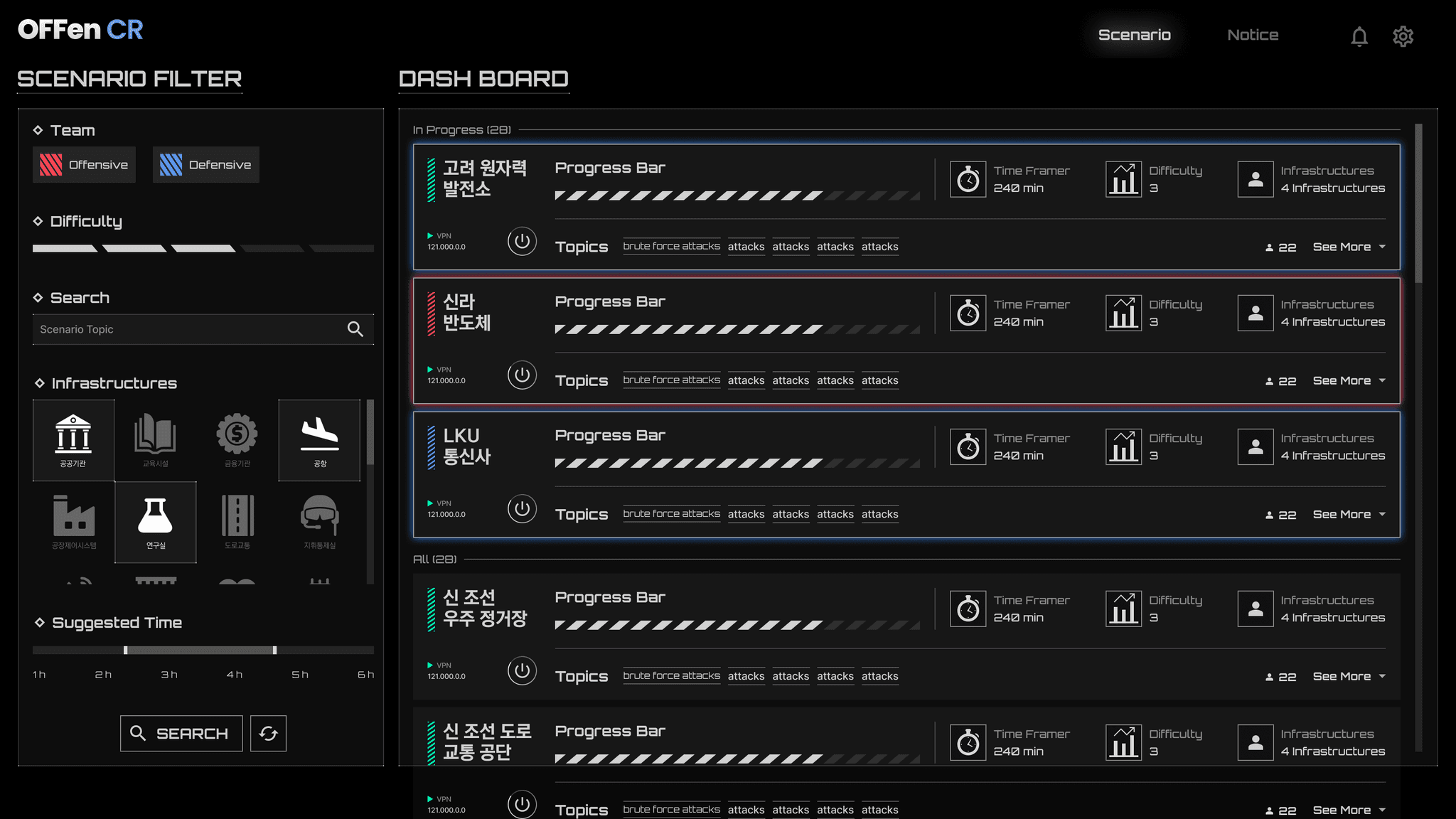
Breaking the existing norm, Discovering and addressing risksOFFen solution
Be different Discover risks firstRespond immediately, OFFen
Through a systematic bug reporting system, you can quickly confirm bug information.
By prioritizing according to importance, it is possible to efficiently carry out tasks.
You can track and manage the process of resolving bugs.
Trusted by the leaders
Major domestic and international companies and institutions are partnering with EnkiWhiteHat.
Expert Driven
Top-Tier White Hackers Delivering Proactive Solutions.
Cutting Edge Tech
Vulnerability reporting rate of 100%Leading the way with excellent technical and practical skillsSetting new security standards.
Trusted Partner
Through Enki's differentiated security solution, customers can enjoy peace of mind.
Trusted by the leaders
Major domestic and international companies and institutions are partnering with EnkiWhiteHat.
Why Working with Us
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of defense industry

“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
CISO of game development company
“With cyber attack threats becoming increasingly sophisticated these days, I was able to learn the latest hacking techniques and defense strategies through this educational program. The practical experience-based lectures by the instructors were very helpful.”
PM of manufacturing company
Trusted by the leaders
Major domestic and international companies and institutions are partnering with EnkiWhiteHat.
What kind of company is Enki (ENKI)?
What does a white hat hacker do?
What is the method for participating in the bug bounty platform, BugCamp?
How is penetration testing conducted and what are the methods and processes?
Why is vulnerability assessment important for businesses?
What kind of company is ENKI?
What does a white hat hacker do?
What is the method for participating in the bug bounty platform, BugCamp?
How is penetration testing conducted and what are the methods and processes?
Why is vulnerability assessment important for businesses?
What kind of company is Enki (ENKI)?
What does a white hat hacker do?
What is the method for participating in the bug bounty platform, BugCamp?
How is penetration testing conducted and what are the methods and processes?
Why is vulnerability assessment important for businesses?
Trusted by the leaders
Major domestic and international companies and institutions are partnering with EnkiWhiteHat.
ENKI WhiteHat is trusted by major enterprises and institutions both in and outside Korea.
Expert Driven
Top-Tier White Hackers Delivering Proactive Solutions.
Cutting Edge
Redefining Security Excellence. 100% Vulnerability Disclosure with Superior Technical Skills.
Trusted Partner
Ensuring a Secure Digital World with Skilled and Ethical White Hackers.
Trusted by the leaders
Major domestic and international companies and institutions are partnering with EnkiWhiteHat.
Quick Links
Contact
biz@enki.co.kr
02-402-1337
167, Songpa-daero, Songpa-gu, Seoul, Republic of Korea
ENKI WhiteHat Co., Ltd.
Copyright © 2025. All rights reserved.
Quick Links
Contact
biz@enki.co.kr
02-402-1337
167, Songpa-daero, Songpa-gu, Seoul, Republic of Korea
ENKI WhiteHat Co., Ltd.
Copyright © 2025. All rights reserved.


























