Protect Innovations
with Expert Insights
ENKI WhiteHat provides unparalleled security
with unrivaled expertise.
Protect Innovation with Expert Insight
Providing unparalleled security
with unrivaled expertise
Protect Innovation
with Expert Insight
ENKI WhiteHat provides unparalleled security
with unrivaled expertise.
ENKI WhiteHat Service
As offensive security specialists, we preemptively address cyber threats from a hacker’s perspective.
As offensive security specialists, we preemptively address cyber threats from a hacker’s perspective.
Offensive Security Consulting
The only way to find out if an enterprise is vulnerable to cyber threats is to view it from the attacker’s perspective. From system failures to customer data breaches, we seek out any cyber threats enterprises face.
Offensive Security Consulting
The only way to find out if an enterprise is vulnerable to cyber threats is to view it from the attacker’s perspective. From system failures to customer data breaches, we seek out any cyber threats enterprises face.
Offensive Security Consulting
The only way to find out if an enterprise is vulnerable to cyber threats is to view it from the attacker’s perspective. From system failures to customer data breaches, we seek out any cyber threats enterprises face.
Cyber Threat Intelligence
We analyze the strategies and tactics used by the four major cyber threat nations—North Korea, China, Russia, and Iran—as well as major cybercrime groups.
Cyber Threat Intelligence
We analyze the strategies and tactics used by the four major cyber threat nations—North Korea, China, Russia, and Iran—as well as major cybercrime groups.
Cyber Threat Intelligence
We analyze the strategies and tactics used by the four major cyber threat nations—North Korea, China, Russia, and Iran—as well as major cybercrime groups.
Cyber Security Training
WhiteHat hackers conduct hands-on training services, from browser and system hacking to reverse engineering.
Cyber Security Training
WhiteHat hackers conduct hands-on training services, from browser and system hacking to reverse engineering.
Cyber Security Training
WhiteHat hackers conduct hands-on training services, from browser and system hacking to reverse engineering.
Trusted by the leaders
ENKI WhiteHat is trusted by major enterprises and institutions both in and outside Korea.
ENKI WhiteHat is trusted by major enterprises and institutions both in and outside Korea.






ENKI WhiteHat Product
Breaking with conventional methods, our OFFen solution detects threats in advance and provides appropriate responses.
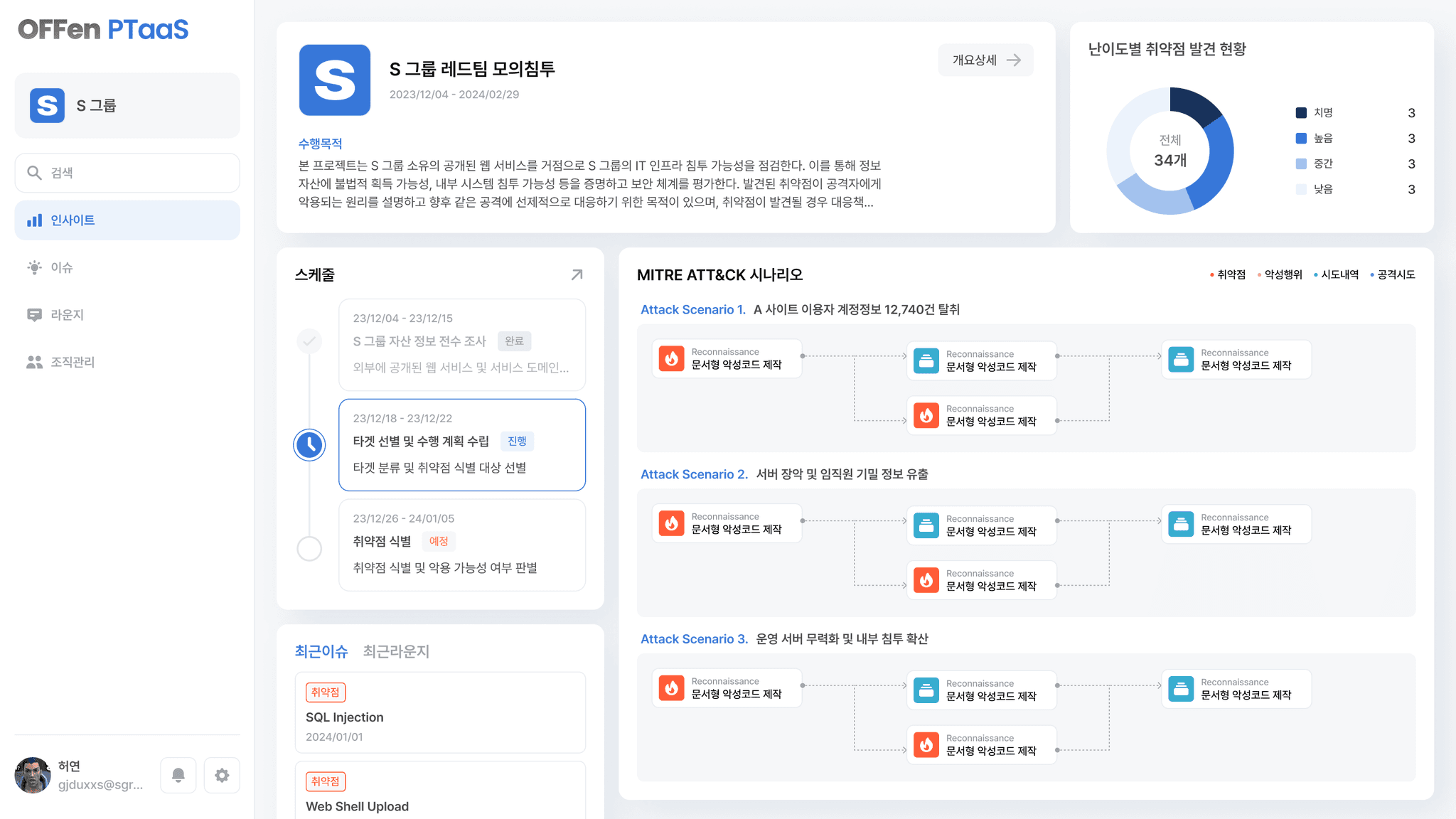
OFFen PTaaS (Pentest As A Service), a subscription-based DevSecOps solution that maximizes problem-solving and collaboration speed of penetration testing
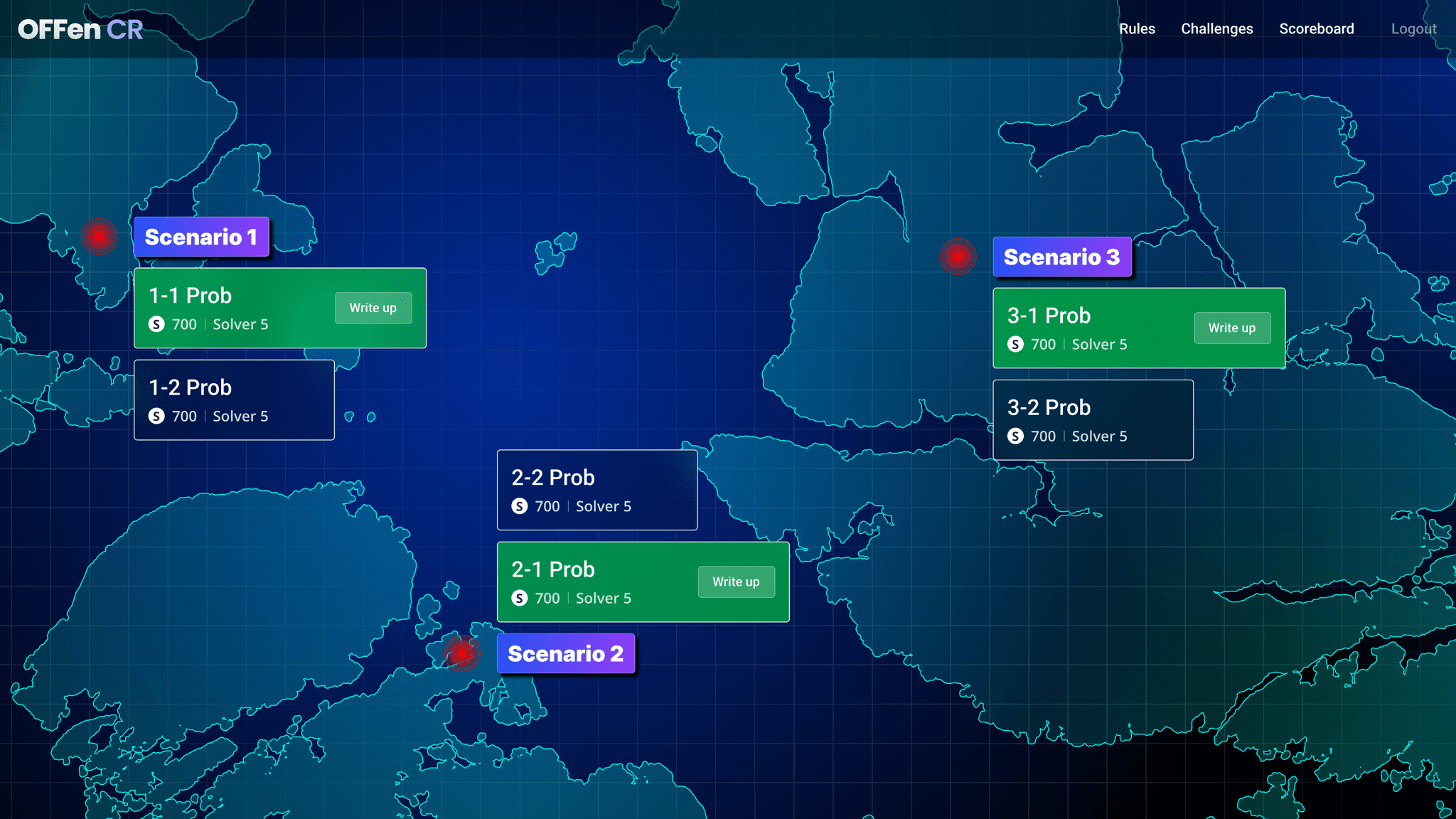
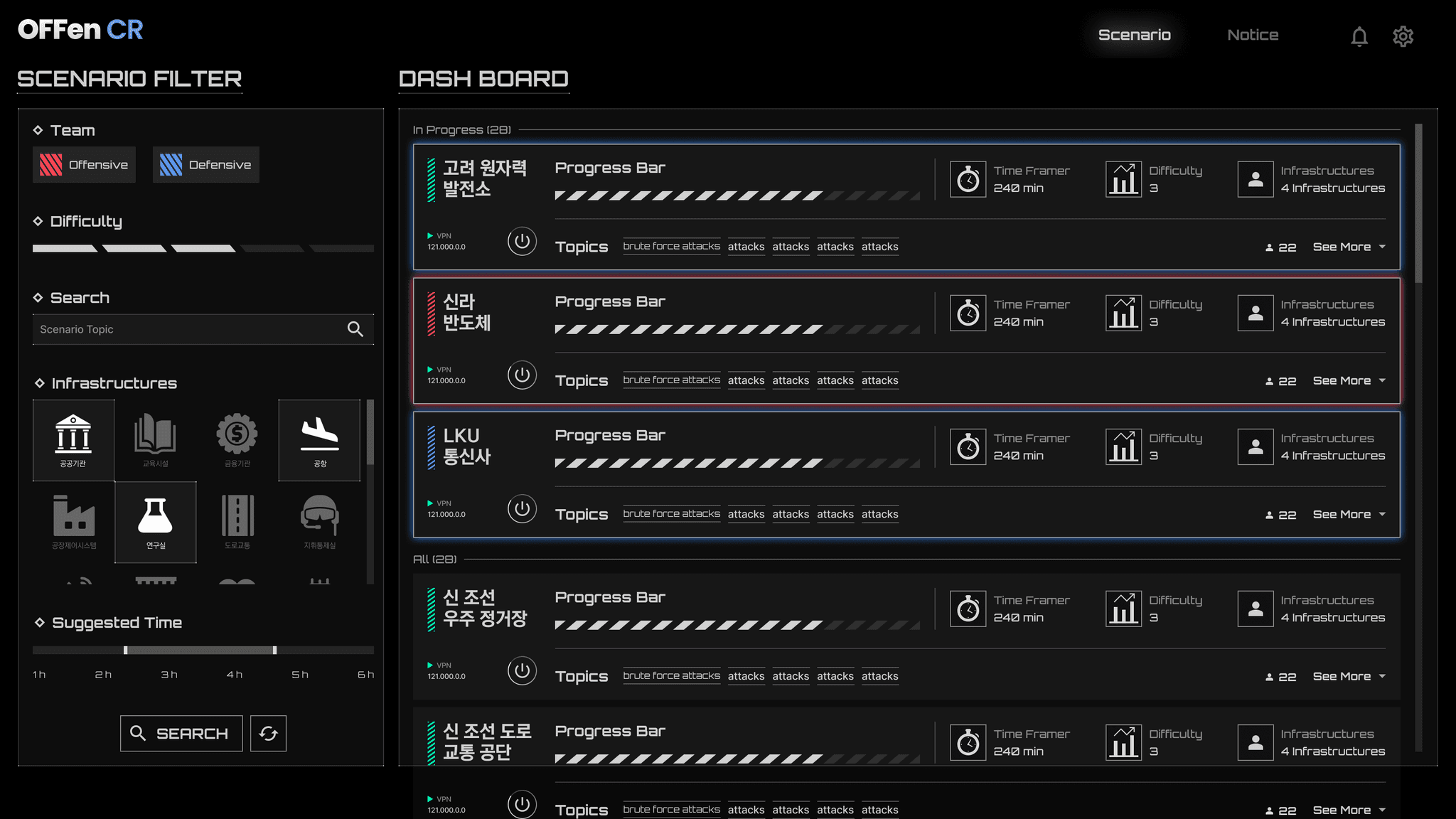
OFFen CR (Cyber Range), a hands-on cyber defense training range solution that recreates actual scenarios for training
OFFen TI (Threat Intelligence), the optimal solution for swiftly identifying the latest security threats and compiling databases of gathered intelligence
The Path We Walked
We provide preemptive response strategies against potential security threats across various industries, supporting sustainable business.
Expert Driven
Our global team of top-tier WhiteHat hackers offers proactive solutions.
Cutting Edge Tech
Equipped with unmatched technical prowess, we provide brand-new security standards and a 100% vulnerability reporting rate.
Trusted Partner
Using both expertise and ethics, our WhiteHat hackers will help create a trustworthy digital environment.
The Path We Walked
We provide preemptive response strategies against potential security threats, supporting sustainable business.
Why Working with Us
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
“After a hacking incident, we ran an extensive hacking simulation to block further attacks and identify hidden threats. ENKI WhiteHat, using creative social engineering scenarios and attack route knowledge, preemptively discovered entry points that hacker groups used and provided clear countermeasures.”
CISO of company K

“For enterprises, implementing a Zero Trust security model is a complex and challenging job. ENKI WhiteHat is a partner fully capable of validating the effectiveness of any Zero Trust security model. The Zero Trust security model, which says, in essence, not to trust anyone, must be continuously validated to remain effective.”
CISO of company N
“Cyberattacks targeting Internet of Things (IoT) devices have surged. Following product development, we conducted penetration testing with ENKI WhiteHat to identify and address vulnerabilities before market release. Fortunately, we were able to enhance our product’s quality and competitiveness using ENKI WhiteHat’s expertise and technical prowess.”
PM of company S
We've got the Answers
We offer Korea’s only Managed WhiteHat Services,
built on a foundation of unrivaled technical prowess and expertise.
We offer Korea’s only Managed WhiteHat Services, built on a foundation of unrivaled technical prowess and expertise.
About ENKI WhiteHat
What do WhiteHat hackers do?
How do we participate in Bugcamp, the Bug Bounty platform?
What types of procedures and methods are used for penetration testing?
Why is vulnerability testing important for enterprises?
About ENKI WhiteHat
What do WhiteHat hackers do?
How do we participate in Bugcamp, the Bug Bounty platform?
What types of procedures and methods are used for penetration testing?
Why is vulnerability testing important for enterprises?
About ENKI WhiteHat
What do WhiteHat hackers do?
How do we participate in Bugcamp, the Bug Bounty platform?
What types of procedures and methods are used for penetration testing?
Why is vulnerability testing important for enterprises?
We've got the Answers
We offer Korea’s only Managed WhiteHat Services, built on a foundation of unrivaled technical prowess and expertise.

Prepare Before a Security Incident Occurs
The Beginning of Flawless Security System, From the Expertise of the No.1 White Hacker

Prepare Before
a Security Incident Occurs
The Beginning of Flawless Security System, From the Expertise of the No.1 White Hacker
Expert Driven
Our global team of top-tier WhiteHat hackers offers proactive solutions.
Cutting Edge
Equipped with unmatched technical prowess, we provide brand-new security standards and a 100% vulnerability reporting rate.
Trusted Partner
Using both expertise and ethics, our WhiteHat hackers will help create a trustworthy digital environment.
The Path We Walked
We provide preemptive response strategies against potential security threats across various industries, supporting sustainable business.
Quick Links
Contact
biz@enki.co.kr
02-402-1337
167, Songpa-daero, Songpa-gu, Seoul, Republic of Korea
ENKI WhiteHat Co., Ltd.
Copyright © 2025. All rights reserved.
Quick Links
Contact
biz@enki.co.kr
02-402-1337
167, Songpa-daero, Songpa-gu, Seoul, Republic of Korea
ENKI WhiteHat Co., Ltd.
Copyright © 2025. All rights reserved.

























